Open-source technologies have become the go-to choice for developers on various development projects worldwide, offering a convenient and cost-efficient alternative to proprietary software. Unfortunately, open source does not come with all the necessary safeguards due to its inclusive nature.
Node.js projects are particularly vulnerable to security issues due to their open-source nature and access to third-party libraries. This article overviews its vulnerabilities and offers potential ways of eliminating them.
Why Node.js Projects Have Security Risks
Node.js has been identified as an ideal technology for web application development. However, due to the use of various open-source packages and NPM repositories, Node.js applications may not be utterly immune to various security issues. Recent surveys indicated that nearly 14% of the NPM ecosystem is prone to security breaches, which can, unfortunately, lead to a massive 54% of affected packages that can compromise Node.js web application security.
While many popular packages are available to Node.js developers, there is no way to guarantee that these components are secure and free from vulnerabilities or malicious code. This means that developers must take extra caution when selecting and using third-party modules in their projects, as even small security flaws can have major repercussions down the line. Furthermore, since Node.js is a relatively new technology, there is a lack of mature tooling available for security testing, which further increases the risk of vulnerabilities being present in the project codebase.
Since Node.js is based on JavaScript, it allows for dynamic code execution, which can create a number of potential security issues, including Cross-Site Scripting (XSS), SQL injection attacks, and Remote Code Execution (RCE). All of these vulnerabilities exist because of the freedom Node.js gives developers who can execute code from different sources without needing proper validation or verification.
Node.js Security Vulnerabilities
By understanding the unique security risks of Node.js and implementing best practices to eliminate them, you can rest assured your project is safe. The hazards that could result in attacks are briefly discussed here, along with some potential remedies.
Denial of Service of HTTP Server
DoS of the HTTP server in Node.js is a well-known security issue that, when present, can seriously impair the performance of an application. A successful DoS attack on a Node.js server can cause it to become unresponsive or minimize its responsiveness to legitimate traffic, which can have severe consequences for the server. When this happens, an attacker can force a server out of service by flooding it with requests and depleting its resource pool.
Mitigations
To prevent this attack, developers should proactively ensure that their Node.js applications have robust input validation capabilities and employ real-time monitoring techniques like rate limiting and generic blacklisting services to protect against CWE-400 vulnerabilities. IT staff should remain vigilant and regularly review audit logs for suspicious activity that could be evidence of a potential attack.
Domain Name System Rebinding
DNS rebinding is a form of attack against Node.js web applications in which a hacker obtains the IP address of a vulnerable application server by using maliciously configured DNS records and exploiting any available vulnerabilities. An attacker can masquerade as a trusted local or external resource and perform actions on behalf of the user in the application. By obtaining responses from the victim’s machine, attackers can access sensitive data or applications. This attack can also bypass certain security measures, such as IP whitelisting and virtual private networks, which can lead to severe consequences for organizations with mission-critical applications.
Mitigations
Although the risk posed by DNS rebinding is significant, it can be easily prevented by using regularly updated web application firewalls and careful configuration of the DNS records. Developers must ensure that their application is correctly configured to verify requesting domains when handling requests from any source other than the local machine. This can be accomplished through various measures, such as validating request headers and restricting the list of accepted domains and IP addresses from which requests are accepted. To help prevent similar attacks from occurring, best practice recommends regularly analyzing code for vulnerabilities that could allow malicious actors to access or modify data within Node.js applications.
Exposure of Sensitive Information to an Unauthorized Actor
The inadvertent exposure of sensitive information to an unauthorized actor (CWE-552) is an alarmingly common mistake that occurs in Node.js development. This attack often occurs during the caching process found in modern web architectures and applications, allowing attackers to access and exploit sensitive information associated even with private APIs.
Overlooking security measures, such as protecting privileged accounts or specific environmental variables and related configurations, can leave them vulnerable to attackers. Critical credentials and data are often exposed if developers fail to be mindful of the security concerns associated with Node.js applications and systems.
Mitigations
To prevent this from happening, it’s important for developers to stay up-to-date on secure coding best practices and take extra caution when dealing with sensitive information. It only takes a small misstep for hackers to have access to your valuable data or resources, so devoting the time to take proper measures is essential.
HTTP Request Smuggling
HTTP Request Smuggling (CWE-444) is an attack technique that allows a hacker to exploit a vulnerability in web applications, giving them unauthorized access. It affects applications built in many languages, including Node.js. To understand this vulnerability, it is helpful to look at both the attacker’s and server’s perspectives: the attacker has two independent requests that “confuse” the server, causing unintended behavior. This can allow them to bypass authentication or load information directly from internal sources instead of through the web application.
Mitigations
To prevent HTTP request smuggling in Node.js applications, developers should use appropriate server-side anti-request smuggling techniques and validation checks before processing any requests. Furthermore, performance and vulnerability testing should be run prior to releasing production code to detect possible flaws or discrepancies in how requests are being handled or interpreted by the server.
Information Exposure Through Timing Attacks
Information exposure through timing attacks, or CWE-208, is a vulnerability in Node.js programming that provides malicious actors with the potential opportunity to monitor data transmitted across a network and discover confidential information within these data. This can occur due to discrepancies between normal execution times of code executions or communication processes which can reveal important details to outside sources.
Mitigations
Developers can choose from an array of techniques to prevent timing attacks in Node.js, such as using carefully crafted algorithms, deploying latency isolation mechanisms, using a constant time string comparison operations, or establishing service timeouts. The use of additional security measures such as encryption and authentication protocols is strongly recommended for all applications running in Node.js environments, especially those working with sensitive information like user IDs or financial records.
Malicious Third-Party Modules
Node.js architecture makes it susceptible to malicious third-party modules. These malicious packages can contain hidden code, credentials, and other malicious attempts at crippling product performance by developers using them. The problem is exacerbated by the fact that they might be popular packages with many external users, and the standard security practices are insufficient to detect these malicious particles.
Mitigations
Developers should use secure coding practices when implementing any third-party module into a Node.js application and ensure they are always up to date with the software provider’s recent security patches and updates. Furthermore, administrators need to ensure secure distribution policies regarding such modules’ installation rights and continuously monitor their use during runtime.
Memory Access Violation
Memory Access Violation, also known as CWE-284, is a well-known vulnerability with serious implications. It involves granting a user access to a protected area of memory that they should not have access to. This type of attack can cause serious damage as an attacker may be able to change or overwrite critical system files and modify permissions on programs and processes, allowing further malicious activity. This can lead to unpredictable behaviors, including crashing the application and exposing users to risk. It can also allow for insufficiently protected data to be accessed and compromised, creating a potential security breach.
Mitigations
To prevent this type of vulnerability from occurring in future software releases, developers must be sure to allocate specific memory locations within the intended range and use secure coding best practices when working with such data. It’s important for software developers and systems administrators alike to stay vigilant against these types of attacks in order to keep their systems secure. Part of staying vigilant includes being constantly aware of any suspicious user activity on the system and taking steps to protect systems by enforcing strict security measures.
Node.js Security Best Practices
So, to make your project secure and free of vulnerabilities, it’s crucial to adopt fundamental Node.js security best practices. Several of those will be covered in this section.
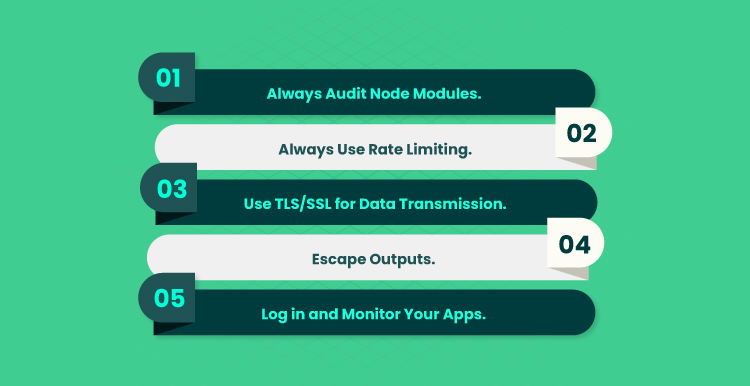
- Always audit node modules. Audit all node modules to ensure the source code is trustworthy and take the necessary measures to protect user data from malicious actors or infiltration attempts. Additionally, regularly review and update the application for further security enhancements, such as introducing preventative measures that can detect intrusion or anomalies in activity or data on your system.
- Always use rate limiting. An easy but important security practice to ensure is rate limiting: limiting how many requests users can make in a given time frame. For example, if you set a rate limit of twenty requests per hour, users will be prevented from overloading the server with excessive requests. This can help protect against unexpected spikes in traffic and malicious attacks. Rate limiting also helps maintain appropriate usage limits for resources such as databases and CPU processes, allowing your app to function more smoothly and efficiently.
- Use TLS/SSL for data transmission. A prime way to secure data in transit is by leveraging TLS/SSL, which uses encryption keys for both authorizations and confidentiality. At Node.js, this type of secure connection is also used to establish integrity and authenticity among partners. This protection helps organizations prevent man-in-the-middle attacks, give delivery guarantees, and protect against any type of modification or manipulation. TLS/SSL is important when building a secure environment for workflows, communication channels, and applications powered by Node.js technologies.
- Escape outputs. Output escaping helps defend against potential cross-site scripting, SQL injection, and other commonly used attack vectors. When using Node.js, it’s important to properly validate user input and escape the outputs that appear anywhere on the page. Utilizing effective techniques such as encoding HTML entities can help prevent security threats and keep your applications reliably secured against attackers. Escaping user inputs and HTML special characters prevents attackers from inserting malicious code into your application, as these practices can stop cross-site scripting (XSS) attacks from occurring.
- Log in and monitor your apps. Keeping an eye on the activity status, errors, warnings, and suspicious actions is essential for running secure apps. End users must be particularly watchful as any unauthorized changes in their system can lead to cyberattacks. By actively logging and monitoring your Node.js apps, you can prevent these malicious activities from taking place and proactively address vulnerabilities found during the testing stages. This might involve installing specialized tools or services that allow real-time tracking of application performance and response times.
Final Word
Understanding the basics of Node.js security is essential for any application developer, regardless of experience level and project size. By taking the necessary steps to secure your Node.js applications, you can protect confidential data and your customer’s information in an ever-evolving cybersecurity landscape.
Forbytes is the go-to provider for businesses that need robust and performant software solutions. Our experienced team specializes in custom software development to meet any needs, yielding projects tailored to individual specifications. Whether you’re at the start of your project or ready to wrap up, our developers have experience delivering excellent results at every stage of the project life cycle.
If you’re ready to get started, contact us today and let us show you what our software solutions can do for your business.

Our Engineers
Can Help
Are you ready to discover all benefits of running a business in the digital era?

Our Engineers
Can Help
Are you ready to discover all benefits of running a business in the digital era?






