The need for effective information security management grows as the world increasingly relies on digital systems. One key component of an effective security strategy is vulnerability testing which companies rely on to identify and fix potential security flaws. But what is vulnerability testing, and how can it be used to improve information security management?
This article will explore the basics of vulnerability testing and provide tips on how to do it right.
Vulnerability Assessment: The Essence
Software products are only as good as the code that makes them up. Attackers are constantly finding new ways to exploit weaknesses in software and hardware. So, to protect their assets and systems, companies must have a thorough understanding of their information security risks.
Vulnerability testing, also called vulnerability assessment, is a process used to identify and assess system vulnerabilities. It is a crucial component of information security management and is often required by regulatory agencies and third-party stakeholders. By conducting vulnerability testing, companies can ensure that they have a solid foundation of information security protections that are up-to-date and effective.
Why Do Vulnerability Testing?
Since vulnerability testing helps your organization identify and fix bugs in the code, it thereby helps reduce the likelihood of security breaches, improving the end product.
In addition, one of the main benefits of vulnerability testing is that it can help businesses avoid the significant financial costs associated with data breaches. In addition to protecting data and assets, it helps businesses comply with industry regulations, such as the General Data Protection Regulation (GDPR). For businesses, vulnerability testing can ensure that customer data is safe and secure and that potential losses related to data breaches are eliminated.
In short, vulnerability testing helps companies improve the performance of their software and reduce the cost of developing new features.
How to Test Your Software for Vulnerabilities?
To carry out a comprehensive vulnerability assessment, you need to have an accurate plan. These fundamental steps can be a good start:
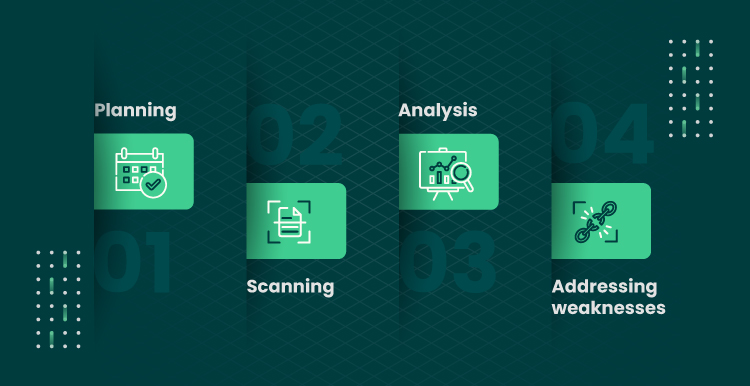
- Planning: When performing vulnerability testing, the first step is to plan out the process. This involves deciding which features and components of the software system will be tested for vulnerabilities and determining the best way to scan for those vulnerabilities.
- Scanning: Once the planning phase is complete, the next step is to perform the vulnerability scan. This involves using the vulnerability testing tool to scan the system for vulnerabilities.
- Analysis: The final step is analysis, which involves analyzing the vulnerability testing results and making necessary corrections. Threats can also be ranked according to severity, immediacy, possible harm, danger, and other considerations.
- Addressing weaknesses: The next stage is to choose how you want to address the vulnerabilities after they have been found and examined. There are essentially two choices: remediation and mitigation. When a threat can be quickly eliminated, remediation takes place. In contrast, mitigation is used to lessen the possibility of a vulnerability if there isn’t a suitable cure or patch available.
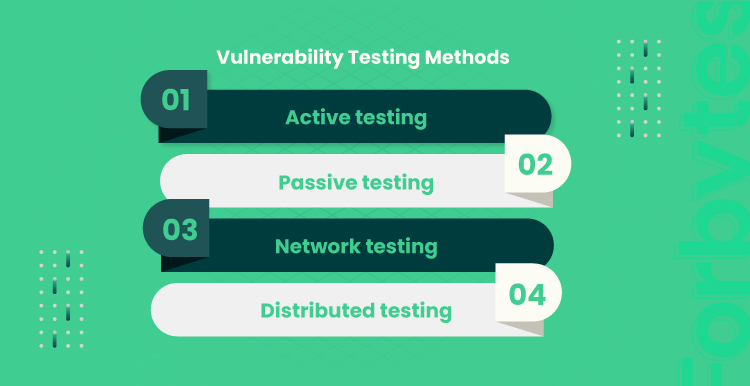
Vulnerability Testing Methods
Different types of vulnerability testing methodologies can be used for different purposes, such as finding the most significant vulnerabilities in a system or determining if the security of a system or network is adequate. Each type of vulnerability testing method has its own advantages and disadvantages and is best suited for certain types of systems and applications.
Active vulnerability testing is the most common type of testing that involves manually testing the system for vulnerabilities. It usually involves white-box testing (examining the source code) and black-box testing with the help of scanners.
Active Testing
Active vulnerability testing is more intrusive, as it involves actually trying to exploit vulnerabilities. Active testing involves the introduction of fresh test data and analysis of the outcomes. The testers build a mental picture of the testing process as they go along, and this model develops further as they interact with the product being tested. The tester is actively involved in learning about new test cases and concepts while conducting the test.
Passive Testing
Passive vulnerability testing uses tools to scan the system for vulnerabilities without user interaction. The scanner provides the user with a report of the vulnerabilities it has identified, and the user can choose to manually test for the vulnerabilities or ignore them. The most common type of passive vulnerability testing is black-box testing, which involves using a scanner to test the system without knowledge of the source code.
Basically, this type of testing relies on monitoring and analysis to identify potential vulnerabilities while using existing test cases and data.
Network Testing
The act of assessing and documenting network operation status through time is known as network testing. Testing is mostly done to forecast how the network will function under “stress” or to identify any issues brought on by new services. It involves using a tool to simulate a malicious attacker’s actions and determine if the system is vulnerable to the attack. The tool generates a report of the vulnerabilities it has discovered, so the user can choose to manually test for the vulnerabilities or ignore them.
Distributed Testing
Distributed testing is testing that is conducted across and between different locations, mostly for testing web apps. In order to perform distributed testing, the test locations must have access to the source code of the system being tested. It is also important that they each have access to the same test data. For example, if distributed testing is performing a black-box test on a web server, then each of the locations must have access to the same web server, which stores the site’s source code.
Vulnerability Testing Tools
The first step in performing vulnerability testing is selecting the right vulnerability testing tools. There are a variety of different tools available, each with its unique strengths and weaknesses. The most common vulnerability testing tools are web applications, network, mobile and desktop application scanners, assessors, and editors. Vulnerability scanners are used to perform automated scanning for vulnerabilities in software systems. An assessor is used to analyze the results of a vulnerability scanner and provide a risk assessment, while an editor is used to modify the source code of a software system to fix the vulnerabilities that were detected by the vulnerability scanner.
Each type of vulnerability testing tool performs a specific type of vulnerability testing. For instance, Burp Suite helps you discover security flaws in web applications, such as cross-site scripting (XSS), path traversal, and command injection vulnerabilities.
Based on the sorts of assets they check, there are four primary categories of vulnerability scanners:
- Network-based scanners: determine weaknesses in wired/wireless networks.
- Host-based scanners: installed on individual machines and can scan for both local and remote vulnerabilities.
- Web application scanners: evaluate web applications to identify safety loopholes, e.g., misconfiguration. They can be used to scan for SQL injection flaws, cross-site scripting vulnerabilities, and other common issues.
- Database scanners: find weak spots in a database to guard against malicious assaults such as distributed denial-of-service (DDoS), SQL injection, and brute force attacks.

Penetration Testing
Penetration testing, also known as ethical hacking, is the process of simulating an attack on a computer system in order to assess its security. This can be done either manually or using automated tools. In a penetration test, the tester tries to find vulnerabilities that an attacker could exploit. Once a vulnerability is found, the tester will attempt to gain access to sensitive data or take over the system.
The goal of penetration testing is not to cause damage but to identify and remediate security risks. In many cases, penetration testers are hired by organizations to conduct independent security audits. By helping to improve the security of a system, penetration testing can play an important role in protecting businesses and individuals from cyber attacks.
Penetration testing typically involves four main steps: information gathering, targeting, exploitation, and post-exploitation. Information gathering is the process of collecting data about a target system, such as its network architecture and software components. This information can be gathered through public sources, such as website registries and search engines, or more invasive methods, such as port scanning and social engineering.
Once a pentester has gathered enough information about a target system, they will begin targeting specific vulnerabilities. Common targets include unpatched software flaws and weak passwords. Exploitation is the process of taking advantage of a vulnerability to gain access to a system or data. Finally, post-exploitation activities may include installing backdoors or malware for troubleshooting purposes.
Penetration Testing vs. Vulnerability Assessment Scanning
When it comes to securing a computer system, penetration testing and vulnerability assessment are two of the most commonly used tools. Both involve attempting to exploit security weaknesses to assess the system’s overall security. However, there are some key differences between the two approaches. Penetration testing is typically conducted by simulating an attack from an external entity, such as a hacker. This allows for a more realistic assessment of how well the system would withstand a real-world attack.
On the other hand, vulnerability assessment is usually conducted by someone with internal access to the system. This allows for a more comprehensive assessment of all potential security flaws, but it may not provide as accurate a picture of how the system would perform in a real-world attack. Ultimately, penetration testing and vulnerability assessment have their own strengths and weaknesses, and the best approach for any given situation will vary depending on the organization’s specific needs.
Both methods have advantages and disadvantages that need to be considered when deciding which is right for you.
Purpose
The tests’ goals are one area where they diverge. A vulnerability assessment aims to determine the current state of a system’s or network’s security, identify where improvements are needed, and prioritize those fixes. Penetration testing aims to find and exploit security vulnerabilities in a system, network, or website. The primary goal of penetration testing is to demonstrate the extent of a security vulnerability and the risk of being exploited.
Testing Service Provider
The agent who administers the testing is another distinction. A vulnerability scan is carried out with the use of many automated technologies. The results are then carefully reviewed and verified by a certified technician or Managed Security Service Provider (MSSP). A penetration test, however, should be carried out by a trained ethical hacker who can access networks and systems using various tools and methods.
Timelines and Costs
Vulnerability scans should be carried out regularly, or at least once every three months, especially after installing new hardware or making other substantial modifications to the programs or system. Although they can be conducted less often, penetration testing is still crucial. They ought to be carried out at least once or twice a year, particularly after adding new hardware or software. Costs for both vary, with vulnerability assessment being somewhat more affordable than penetration testing because it is smaller in scope and usually less thorough.
Output
The result of a vulnerability assessment is a report that lists any vulnerabilities that might be used against the system. A penetration test report ranks vulnerabilities as high, medium, or low to indicate the degree of risk and potential exposure. It indicates what serious flaws may be exploited, how they might be done, and what information might be compromised.
Whichever approach you choose, periodically reassess your system’s security to ensure that it remains strong in the face of ever-changing threats.
Final Word
A secure and reliable information infrastructure is more critical than ever in today’s fast-paced world. Vulnerability testing is vital to ensure that your software development company is doing everything possible to protect its customers’ data. It ensures that your company’s products are secure and potential threats are identified and fixed in time.
Contact us if you need help ensuring your IT infrastructure security, and we’ll gladly help you!

Our Engineers
Can Help
Are you ready to discover all benefits of running a business in the digital era?

Our Engineers
Can Help
Are you ready to discover all benefits of running a business in the digital era?







