React.js is a compelling JavaScript library used to make user interfaces, web applications, and many more. Security should always be a top priority when working with these open-source libraries. However, security threats and vulnerabilities can be overlooked or neglected.
This guide provides an overview of the potential security threats related to React.js and ways to fix them to maintain the highest level of security possible. Being aware of these issues can significantly reduce the risks for your application. You will understand what challenges you may face and know how to tackle them.
Why Should You Keep an Eye on React Security Vulnerabilities?
Security vulnerabilities can bring great harm to organizations and individuals if not addressed in a timely manner. Highly skilled threat actors may be able to manipulate computer security flaws to gain unauthorized access or otherwise affect operations. These threats can take various forms, from system modifications that introduce malicious code into a website or application, to sophisticated remote attacks orchestrated across multiple networks. It is therefore essential for organizations and individuals alike to pay close attention to security updates and patch management protocols in order to mitigate any potential risks associated with identified vulnerabilities.
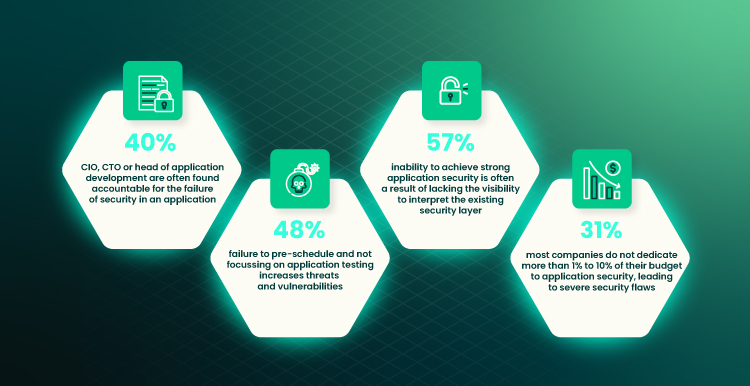
As one of the most popular web development frameworks in use, React provides countless developers with the ability to build performant and responsive applications. While its features are beneficial to many creators and users, keep an eye on security vulnerabilities as hackers can sometimes exploit newfound loopholes. It’s important to act quickly on these specifications, as if overlooked, React could suffer catastrophic security breaches. To counter this threat, take the time and research expert opinions as well as solution guides online. By proactively maintaining a watchful eye towards React security vulnerabilities, you could prove invaluable in preventing further damage.
Common React Security Threats and Ways to Address Them
React.js is a powerful JavaScript library embraced by many developers. However, it is also prone to an array of potential security issues. These may include Cross-Site Scripting (XSS), broken authentication and authorization, risky code injections, misconfigurations, lack of secure coding standards, and third-party components with vulnerabilities.
Let’s take a closer look at the most common React security vulnerabilities and find efficient ways to fix them.
SQL Injection
SQL injection is a serious threat to the security and integrity of applications built with React, an open-source JavaScript library. This type of attack, which is categorized as code injection, exploits vulnerabilities in the underlying SQL implementation by directly accessing the application’s database. It allows malicious users to gain access to otherwise restricted sensitive data and modify or delete existing information. As such, preventing this type of attack must be a top priority for those developing React-based applications. Developers should review their code carefully to ensure all user input is properly sanitized before execution, while also regularly testing and updating their software with the latest security patches.
React applications are at risk when accepting user-submitted input that is not properly checked and sanitized, as attackers can take advantage of this to access a database directly. To combat this security vulnerability, developers must use defensive coding strategies, including proper input validation and maintaining up-to-date software with the latest security patches. Additionally, emerging technologies such as web application firewalls may be deployed to detect malicious attempts in real time and prevent adversaries from achieving their goals by blocking traffic or preventing data leakages. Understanding the risks and taking steps to protect against them is vital for any organization that uses React.
Broken Authentication
Broken authentication is a very common security threat and is especially prevalent in React applications. By failing to provide secure credentials, unauthorized users can gain access to protected resources. Hackers have been known to exploit weak authentication systems, such as usernames and passwords that are stored without encryption or stored in publicly accessible locations. If your organization uses React applications, it’s essential to develop robust authentication protocols, such as using tokens and multifactor authentication that limit and control access to resources only to those who have the authority. The best defense against a broken authentication attack is a proactive approach that focuses on prevention – investing in up-to-date security protocols can help protect organizations from the devastating consequences of the attack.
Broken authentication systems can be difficult to troubleshoot and fix, particularly when embedded in React applications. It is important to understand the principles of authentication in order to ensure the system security. To begin a successful repair process, developers need to evaluate the application’s current settings, review any available logs, and audit their code for vulnerabilities. In addition, they should action proactive measures to keep their React application’s authentication system up-to-date. This includes implementing complex passwords, implementing rate limits, disabling passwords after multiple failed attempts, and using two-factor authentication methods. Taken together, these steps will help developers create an optimized authentication system that can reduce the chances of unwanted access.
Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is a major security threat to any application built with React. It occurs when attackers inject malicious client-side scripts into pages visible to other users. Such attacks can be used to steal user data and override existing content, putting the privacy of app users at risk. Developers need to ensure XSS risks are mitigated within React applications by using strict validation rules for user input, sanitizing dynamic content, and auditing existing code for vulnerabilities. Furthermore, it is essential that updates are regularly applied as soon as possible since attackers constantly develop new ways to exploit even the most secure applications. With vigilance and vigilance, developers can prevent XSS from becoming an issue in their React projects.
Cross-Site Scripting (XSS) is a common vulnerability in web applications, and it’s equally dangerous in React applications. Fortunately, there are ways to fix XSS issues in your React application. First and foremost, you should upgrade your code by using user input sanitization – this is the process of removing anything that could be used to exploit an XSS attack. Additionally, executing a content security policy with extra headers might also be a good idea if you’re serious about preventing malicious attacks on your website. Finally, always use the strictest security protocols available when creating React applications, otherwise, it may lead to data leakage or the creation of backdoors for malicious actors. By ensuring you address any XSS vulnerabilities quickly and efficiently, you can make sure your React application is safe from any potential attackers.
Cross-Site Request Forgery (CSRF or XSRF)
Cross-site request forgery (CSRF or XSRF) is a major security threat in the React framework. Put simply, CSRF occurs when an attacker is able to trick a user into executing an unintended action on an authenticated website due to the lack of anti-CSRF protection. By taking advantage of the user account’s pre-existing authentication cookie, attackers may be able to create malicious requests that perform privileged operations without any direct interaction from the victim. To ensure adequate protection against such exploits, web developers should implement preventive safeguards like using randomly generated “secrets” or tokens stored in the session state and validating their presence with every request. These measures can combat powerful threats like CSRF and provide additional layers of security for React applications.
React is a popular technology used to render user interfaces and build powerful web applications. However, security risks always remain a concern in any application. Fortunately, Cross-site Request Forgery (CSRF or XSRF) is an attack vector that can be mitigated with the implementation of best practices in React. The primary defense against CSRF is to cryptographically verify requests coming from a browser. This can be achieved by validating anti-forgery tokens provided by the server while making API calls. Additionally, using proper headers such as “X-Content-Type-Options: nosniff”, and “X-Frame-Options: DENY” can help prevent most forms of CSRF attacks in React applications. As such, any application that leverages React should follow these guidelines to protect itself against CSRF attacks.
Zip Slip
Zip Slip is an alarming React security threat that can attack applications and put confidential information at risk. This security flaw arises when a supporting library unpacks files in an uncontrolled manner, making it easy for malicious actors to place malicious code inside unzipped folders. In addition to this, affected versions of Zip Slip allow the potential attacker to write files outside of the intended destination and gain access to other areas of the application’s code. Through these extremely dangerous means, an intruder could access sensitive data like passwords or other valuable files that should remain private. Thankfully, developers have already identified the issue and created mitigation techniques that can be applied in almost all cases. Although it won’t guarantee absolute protection against such threats, applying safeguards as soon as possible is the best course of action to ensure that React applications are shielded from such vulnerabilities.
React developers should be aware of the zip slip vulnerability, a type of path traversal attack that can allow remote code execution. Zip Slip can inexpensively and easily be fixed by paying attention to the filenames passed to any system call. Specifically, whitelisting user input so only certain absolute paths can be given is a great way to prevent this type of attack. Regular risk assessments and security auditing can ensure that security controls are implemented in all areas where React is used and log reviews should continuously monitor for unauthorized file access or changes. Taking these steps will help protect against Zip Slip in React-based systems.
XML External Entities (XXE)
XML External Entities (XXE) is a type of security threat that can be found in web applications built with React. This attack occurs when an XML document containing an external entity reference is processed by an XML parser within both client-side and server-side applications, allowing attackers to gain access to system resources, upload malicious files, or potentially disclose confidential information. Developers must ensure that all React applications are free from vulnerabilities associated with XXE attacks. When developing React applications, best practices such as disabling external entity references or validating user input for malicious content should be employed in order to protect against this security threat. Taking the necessary steps to ensure that your React application is secure from XXE threats is essential for providing a safe environment for users of your application.
XXE is a type of vulnerability present in web applications that allow attackers to gain access to sensitive system files. React developers need to take special care when reading XML documents as XXE can be unintentionally enabled during the processing of external entities encountered in the XML data. The first step is to ensure that the document type declaration (DTD) is explicitly stated and locked down to prevent any potential XXE attacks from happening, especially with legacy libraries. Additionally, all XML documents should be validated before being processed and interpreted, along with proper encoding considerations taken for particular characters – such as for those involved in the referencing of external entities – when parsing XML-based formats. Finally, a dedicated security tool should be employed to perform regular scans across an entire application code-base and any external integrations, using established best practices and code-level security standards, thereby helping to protect against XXE attacks.
Vulnerability in Packages and Dependencies
A potential security threat facing those who use React is the vulnerability of packages and dependencies. This risk can be particularly damaging to enterprise applications as malicious actors may exploit known flaws or vulnerabilities in third-party libraries. As such, developers should take the time to audit their applications for any insecurity that may be present in their libraries and packages. Further, proactive reviews of external third-party sources should be conducted regularly to detect and remediate security risks before they are exploited. It is essential for users of React to responsibly manage their application’s dependency chain in order to protect it from malicious attackers aiming to undermine their system’s security.
React is increasingly becoming a popular go-to choice for developers. Its popularity comes with a downside, as it’s becoming an attractive target for malicious third parties to exploit. This exploitation can come in the form of vulnerable packages and dependencies when building React applications. To protect against such attacks, it’s important to keep a keen eye out for vulnerable packages and dependencies in your React applications. Regular updates should be done for all of the dependencies used in your application, both large and small. Additionally, regular security scans should also be performed to ensure that full protection is received against any potential threats or vulnerabilities present inside the application. With these steps in mind, you can rest assured that you have taken considerable efforts towards addressing any concerning issues related to package and dependency vulnerabilities within React applications.
Final Word
With all the advantages of React.js, such as speed and flexibility for user interface development, web developers need to stay attuned to potential security threats and vulnerabilities. Fortunately, there are ways to eliminate them by regularly keeping up with updated versions of the framework, properly validating user inputs, isolating variables in different parts of the application stack, implementing secure server-client communication protocols, adding authentication layers whenever possible when working on public applications, and testing their code.
By utilizing these basic methods of increased safety, any React.js project can be securely managed while taking full advantage of its many benefits.

Our Engineers
Can Help
Are you ready to discover all benefits of running a business in the digital era?

Our Engineers
Can Help
Are you ready to discover all benefits of running a business in the digital era?






