The explosive and widespread adoption of the Internet has brought a series of fundamental changes to the security landscape. Understanding the types of vulnerabilities that a web app is vulnerable to is important to protect yourself and your customers.
This blog post will explore the different categories of web application vulnerabilities and the ways in which organizations can protect their data.
What Are Web Application Vulnerabilities?
The growth of the Internet and changes in technology has brought about a new era in which web-based technologies take center stage in every field. The advances in web app technologies, in particular, brought about a new era in which we find ourselves in danger of a cyber-security breach every day. Today, it’s anything but unusual to hear about a cyber attack.
Web applications are experiencing a record number of security breaches every year. The stats below depicts the number of compromised data records in selected systems as of January 2021.
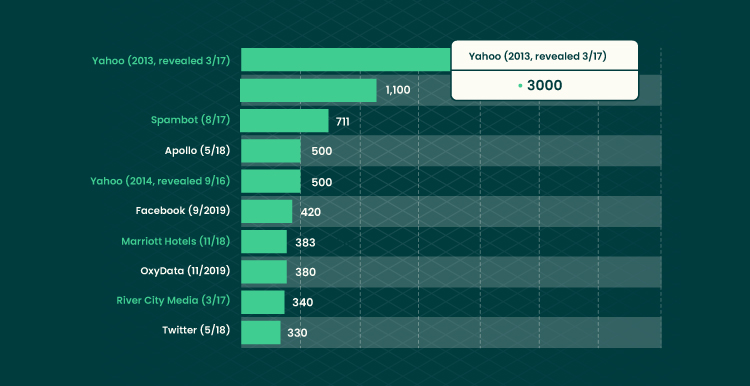
According to Statista, 18.2% of the Internet that encounters critical vulnerabilities is associated with cross-site scripting attacks.
A vulnerability is a weakness in a system or application that could be exploited from the outside to gain access to data or cause unexpected behavior within an application. Generally, software that interacts with the Internet and uses web technologies, like HTML and CSS, is prone to security issues. Vulnerabilities are flaws, glitches, malfunctions, or errors that affect the software, system, or network, such as a computer or device.
Here are the most common web app vulnerabilities by PTsecurity:
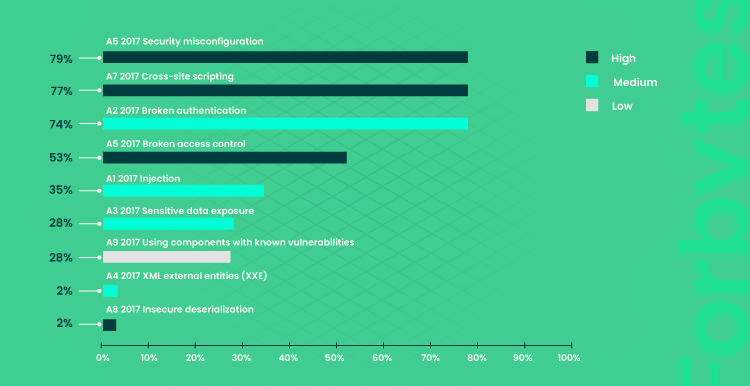
Webapplicaties security vulnerabilities mean the situation when hackers or a third party are able to gain access to a system and use it in an unwanted manner, changing the way it functions or deleting it. These are the categories of weaknesses in web applications that an external entity could exploit to compromise the security of a system.
Web application vulnerabilities are sometimes classified with terms such as bugs, security flaws, weaknesses, flaws in the software, and vulnerabilities in the computer program. Hackers can exploit weaknesses in a web app, which can lead to data leakage, data corruption, or tampering with data. This, in turn, poses a high risk to organizations.
Hackers can use various ways to harm your business. Each of the pathways below poses a risk that may or may not be a severe threat to take action against. However, web applications are also computationally very expensive for attackers to breach. This is an example of a security breach scheme:
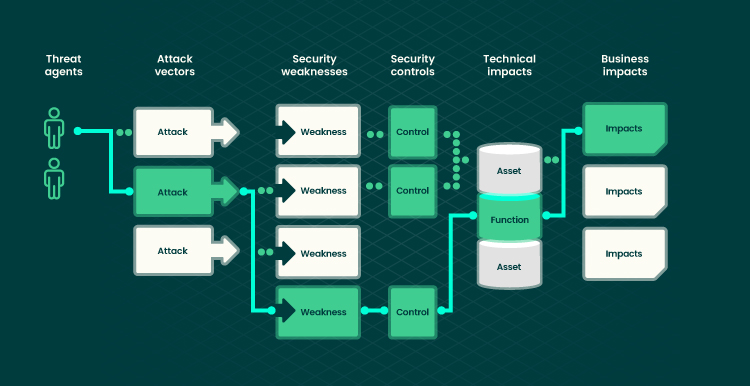
Interest in web application vulnerabilities is increasing because these typically have the highest rate of impact on the business in terms of the number of lost customers. Vulnerabilities usually have a direct or indirect impact on the user experience.
Common Web Application Security Vulnerabilities
Web application vulnerabilities are not that different from the vulnerabilities found in any other application. They focus on the communication protocols, browsers, and underlying operating systems. Let’s take a look at the most common web app vulnerabilities and ways to eliminate them.
Broken Access Control
Access control refers to the process of defining and enforcing the rights of users and guests visiting or using a website or web application. It limits access and permissions for all components (database, web server, programming, etc.) in such a way that users cannot access the content they should not see. As a result of this vulnerability, legitimate users of a system can access records of other users and update or distribute sensitive information.
Vulnerabilities like this one have raised alarms with businesses concerned over the potential loss of proprietary information, hackers being put on exposed pathways, and a significant impact on financial returns. Whether you are purely an individual consumer or scaling production on a large scale, these are concerns that all users should understand.
Prevention
From IP address to access permissions, web applications need to ensure that only authorized users are able to perform the desired actions.
- Improve access control: this one should work on the server-side using ACL and role-based authentications.
- Disable access to default features: users shouldn’t perform any actions with any of the functionality that isn’t disclosed to them.
Injection Flaws
Injection flaws in web applications are one of the most common cyber security threats. They allow attackers to take complete control over the application running on a server. They normally take the form of injection attacks and SQL injection attacks. Web apps, especially web applications with public-facing live APIs, are vulnerable to injection flaws that allow an attacker to exploit a web app’s programming vulnerabilities and used them to access sensitive data.
Injection flaws allow an attacker to bypass authentication mechanisms and gain unauthorized access to an application. This can result in exposing customer or end-user data or exposing client-side code in JavaScript, which can allow an attacker to take over the client-side application and cause it to perform undesired actions or even make an app shut down.
Prevention
Developers and website admins should have knowledge of programming, web architecture, and database design to prevent such application security vulnerabilities from occurring.
- Verification of entered data. Input verification averts incorrectly generated data from entering the system. Therefore, when attempting to avert injection flaws, it is very important to check all the data entered.
- Statements sets with parameterized queries. This is an adequate method to prevent SQL injection. Certain parameters are not set when the statement is created but are added at runtime. Therefore, attackers cannot change the request, even if they issued a command themselves.
- Restricted user rights. You do not always need to connect to the database utilizing administrator accounts. To eliminate the likelihood of an injection, database users should only have the most necessary privileges. For instance, it is best to give them access solely to a certain database without the ability to generate or modify data in the tables.
Cipher Transformation Insecure
A vulnerability in Cipher, the AES-based encryption software, can be exploited by an attacker to decrypt any file encrypted with a long-term public key. The vulnerability is classified as a cipher transformation insecure vulnerability. When the encryption scheme that was used is faulty, the decoder algorithm can be used to find vulnerabilities in the system.
The cipher transformation insecure vulnerability (CVE-2017-15326 in the NVD) was found in the OpenSSL library operating as an SSL/TLS server that remote attackers might exploit to disclose sensitive information. This vulnerability allows attackers to expose or manipulate sensitive data or make modifications to secure information to which a user should not have access.
Prevention
Strong encryption is important for app security and the privacy of users. So, if the algorithm you’re using right now has undergone an attack, consider using a stronger one, such as AES. The decision whether to migrate your users to the newer encryption algorithm is ultimately up to the CIO of your organization. They must take into account the total cost of the data migration.
Also, when it is possible, you should apply integrity checking with HMACs. Integrity checking is a password hashing function that uses a cryptographic hash algorithm. HMACs use a cryptographic hash function and a secret key to produce a hash value that can be compared to the input value.
Cross-Site Request Forgery
A cross-site request forgery is a type of malicious computer code executed by a website that allows a hacker to steal information and control user behavior by passing messages, accepting cookies, or running scripts on behalf of a legitimate website visitor. In fact, it’s a computer fraud that occurs when one web page causes another web page to perform an action of the attacker’s choosing.
An attacker tricks a vulnerable web application into performing an unwanted action on a different website that the attacker controls. The action is typically sensitive data theft, such as stealing passwords, credit cards, or other confidential information. A malicious web page embeds a specially crafted request for a non-authenticated resource on a web server on its page. This resource could be a file, script, or even another web page.
Prevention
There are available measures to prevent CSRF attacks in your application. By using secret tokens or cookies, you can avoid receiving invalid requests, or malicious ones, from the online users whose identity you are authenticating. You could use only POST requests, assisting the URL is not getting compromised.
Cross-Site Scripting Attack
Cross-site scripting attack is an attack on your website in which a hacker looks for application security vulnerabilities of your website and then exploits them. They hack in the form of a browser exploit and inject scripts into your website that can change the website content. This type of computer security vulnerability is typically found in web applications that involve a website allowing and then facilitating the execution of client-side scripting on content the website itself does not control.
Cross-site scripting attack is primarily caused by incorrectly encoded user-supplied data. But they can also arise from certain buggy web server software or security vulnerabilities in web applications. In web browsers, the injected script can alter webpage content, or a hacker can inject malicious code into a trusted website. This code can perform a variety of tasks, including stealing data or providing a quick way to own your account.
Prevention
- Escape: ensure all inputs are properly escaped before they’re rendered in the web browser. This helps lower the risk that incoming data will be misinterpreted or interpreted in a malicious way.
- Validate: Validation is to ensure that a web app is rendering the correct data and producing the desired output. Whitelists, which are typically employed to prevent injections, may also be helpful in this case.
Encapsulation Vulnerability
Encapsulation vulnerability is the name of an attack that exploits the way in which a web application binds to a specific interface. This binding will open access to all functionality, but it also means that if that functionality is exposed to the outside world, the attack exposes every bit of confidential data in the application. Attackers can exploit this vulnerability to extract database contents, modify database contents, lock out database accounts, and terminate systems.
Apps are extremely vulnerable if they can’t isolate or determine essential data or functions within components. For instance, enterprise resources are generally stored in database tables for easy access and maintenance. The database tables are often drawn from a single web application. By taking advantage of a database’s data storage, an attacker can retrieve all database content from a single web application. This problem is known as database encapsulation vulnerability.
Prevention
Identifying the encapsulation vulnerability is possible if a company reduces access to the app database or system up until full danger remedy and protection. Backups allow companies to restore the working environment without making the payment required by an attacker.
Failure to Restrict URL Access
Failing to restrict URL access is one of the most common online security mistakes of recent years. URL access control, or URL access restrictions, is an important component of cybersecurity, especially for public websites and apps. Restricting URL access not only protects against unauthorized access, but also prevents the display or use of that website in an unauthorized manner such as phishing, malware distribution, or spreading misinformation.
What is a URL redirection or URL redirect? When a URL has a rather obscure (and often problematic) URL redirect, it means that a request to visit the original URL is redirected to a different location. The result of a spider or link popularity page visiting the URL redirects causes problems as the URL has generally been popular due to the issue.
Prevention
One of the smartest things to do when you set up a website, blog, or anything else that you share with the world is to restrict access to specific URLs. This allows you to maintain some level of control over what people can interact with.
We’ve put together some handy tips on how to protect your application security and what to do if you spot a URL access issue:
- Set role-based access to reduce the measures necessary to maintain authorization policies.
- Configure policies in a reliable way to reduce any strictly coded elements of policy.
- Prohibit any default access, demanding the direct provision of certain users and roles to access each page.
- Make sure that web pages that are undergoing an operation are in the state to allow access.
Final Word
The increasing popularity of websites with web applications has led to security concerns and the need for web app monitoring and audit services. As it becomes easier to create and share web applications, the risk of having dangerous content grows in tandem. But prevention methods exist, and they should be elaborated on and improved in the future.
We hope that now you know how to eliminate the most common threats to your web apps. If you have any questions left on web application security and safe data management, contact us, and we will help you!

Our Engineers
Can Help
Are you ready to discover all benefits of running a business in the digital era?

Our Engineers
Can Help
Are you ready to discover all benefits of running a business in the digital era?







