Digital transformation in ecommerce makes trade borderless and effortless. Customers can purchase goods globally using a mobile device and choose the best for the best price. But this is only one side of running an online business. Another side is the cybersecurity threats associated with the e-commerce industry.
Common e-commerce security threats are exactly what we’ll discuss in our new article. They can be very complex and consistent and may go far beyond the well-known brute force attacks.
E-commerce Cyber Security. Why Do You Need It?
In 1999, Kalakota and Whinston coined the term ecommerce. It refers to buying and purchasing goods, services, or information via computer networks. This was the end of the 20th century when broad masses started gaining benefits from online trade… and when security vulnerabilities began to accompany the online activities of average users. The more opportunities people were given, the more they had to be concerned with data privacy in e-commerce.
No matter if you have recently started an ecommerce business or already managed to earn a stable position in the market. You need to care about security anyway. Here are the reasons:
- Technology drives rapid changes, and rapid changes drive new problems. In an environment where new things appear every day, static solutions are ineffective. Old problems undergo a transformation, while new security problems continue to appear. You can do your best to take common measures to secure your ecommerce website and consumer data. But anytime, you need to be ready to improve your solutions and upgrade your strategy to cover broader security needs.
- Businesses invest in competition and not security. E-commerce is a highly competitive market. Online businesses tend to leave the cybersecurity question behind. They focus on fighting competition on different ecommerce platforms. When doing so, enterprises lose the understanding that two notions are related to each other. In reality, high e-commerce cybersecurity improves the brand’s reputation and increases client trust. This, in turn, affects competitiveness.
- Security is viewed as an extra goal and not the main one. There is a lot in common between traditional commerce and online commerce. However, the latter is characterized by higher e-commerce threats. This is why businesses need to put client security first. Customer data and money, as well as profit security, depend on how secure an e-commerce website is.
Kalakota and Whinston, who coined the term e-commerce in 1999, also talked about e-commerce security. They differentiated between two aspects of e-commerce security:
- Client/server security. This aspect of e-commerce security refers to the interaction between a client and a server. Companies are required to stick to the industry data security standard. E-commerce businesses integrate various mechanisms to prevent third parties from accessing confidential data. These include but are not limited to the use of passwords, biometrics, data encryption, firewalls, etc.
- Data/transaction security. The protection of payment data is of utmost importance for ensuring website security, privacy, and integrity. Businesses should not underestimate this aspect. Insecure transactions may lead to data replication, modification, and loss. The BaaS market is growing, and consumers today demand that e-commerce service providers ensure the safety of their credit card data. Also, they want to be 100% sure that businesses use only secure electronic transaction methods.
So, your task is to ensure that your transaction and data security is on a high level. Consider improving the following aspects of cyber security in e-commerce:
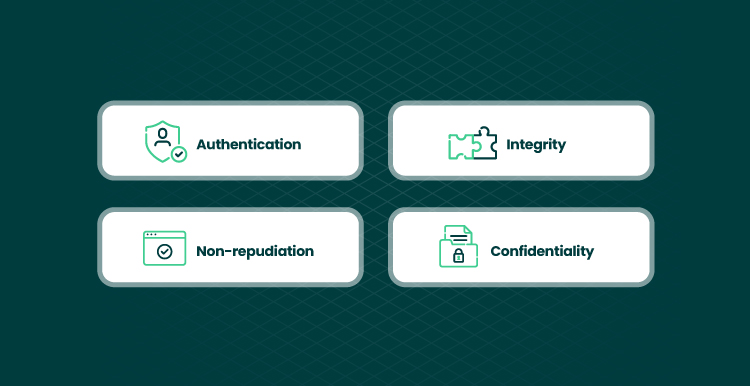
- Authentication. The authentication process guarantees that a particular user is authorized to take a specific action. Authentication is based on identifying user attributes that are tested against a set of permissions. This is implemented in challenge-response actions, the use of passwords, and cryptographic keys.
- Integrity. Integrity determines the level of data protection on both sides: the service provider and the customer. Data integrity prevents situations when data is modified on one side and get opened to new cyber threats while another side has no evidence of it.
- Non-repudiation. This aspect proves an action to be irrefutable. Non-repudiation is evidence of a buyer taking a particular action in relation to a seller. Non-repudiation lies in the use of physical signatures in traditional commerce. Or the use of digital signatures in online commerce.
- Confidentiality. This ensures that the interaction on e-commerce websites is not accessed by non-authorized parties.
Neglecting cyber threats and risks in custom e-commerce development may result in the following:
- Adverse effects on a company’s reputation. Clients don’t trust e-commerce businesses if they use untrusted networks or unreliable tools.
- Financial fraud. An unauthorized third party may gain access to your finances.
- Lower competitiveness. Your target audience will choose an e-commerce store with higher cybersecurity.
- Legal responsibility. You may have legal troubles if someone loses their data or money because of the ineffective security protocols on your e-store.
Reasons for Cybersecurity Threats. Why Do They Happen?
We’ll talk about 3 reasons why cybersecurity threats exist and why businesses need to invest in problem elimination.
Gaps in Software Security
This type of e-commerce security risk is inherent to the software written in an insecure manner. In some cases, developers neglect e-commerce security issues intentionally. In other cases, they do not devote enough time to implementing e-commerce security measures to protect the software. Sometimes, for the sake of quick development, they simply copy high-risk code blunders shared in open source. The use of malicious code increases the chances of security holes, which experienced website hackers can misuse.
Solution: Request a security audit from an ecommerce consulting company. Professional software engineers will test your software against different kinds of security threats. They will make a plan for boosting the security of the whole network.
Gaps in Physical Security
This cause is relevant in situations when unauthorized agents get physical access to confidential data or a network. The reasons for this happening can lie in the neglect of physical security measures or a careless interaction with a system. For example, people may suffer from password abundance. Thus, they decide to save all their passwords in one place or duplicate their login credentials across systems. By gaining access to such data sources, penetrators may steal passwords and use them for malicious purposes.
Solution: As an ecommerce website owner, you need to provide your employees only with secure hardware and software. Make sure that the computers they use at work are secure, as well as the printers and tools they access. Also, a good idea is to limit login attempts and set access control. This will help you keep the process of entering the system clear.
Poor Management or Misuse of e-commerce Services
Poor management of enterprise software is a common reason for e-commerce security issues. Sometimes, employees neglect the security measures dictated by their company. This leads to the emergence of the so-called e-commerce security holes. For example, an employee does not update the latest version of patches or leaves the system open for third parties. One more reason why vulnerabilities of this type occur lies in the hardware. The hardware used for management may be incompatible with the software.
Solution: Prepare clear security guidelines for your team. Make sure that they implement e-commerce security best practices. Update these practices when your security strategy changes or your software gets updated.
Cybersecurity Threats: Types and Examples
The list of security issues of e-commerce may seem endless. This is why we need to categorize them. There are 4 main types of e-commerce cybersecurity threats based on the nature of the threatening action:
- Active: actions are taken to introduce changes to a system or software;
- Passive: do not change the integrity of a system; are linked to the loss of confidentiality;
- Accidental: breakdown of hardware or errors in software;
- Intentional: an unauthorized third party intentionally damages a network to perform cybersecurity crimes.
Intentional threats — this is what interests us the most. These are very common in today’s online environment. For instance, sabotage is a widespread intentional cybersecurity threat. This is when unsuspecting users share a virus program with others. This leads to the loss of connectivity and access to network services.
DoS is an example of how intentional threats work. DoS, or denial of service, makes service unavailable and the whole system unable to provide usual services. This may be achieved by flooding the network with an abnormal volume of traffic. As a result, people cannot use the e-commerce website legitimately.
Phishing and Pharming
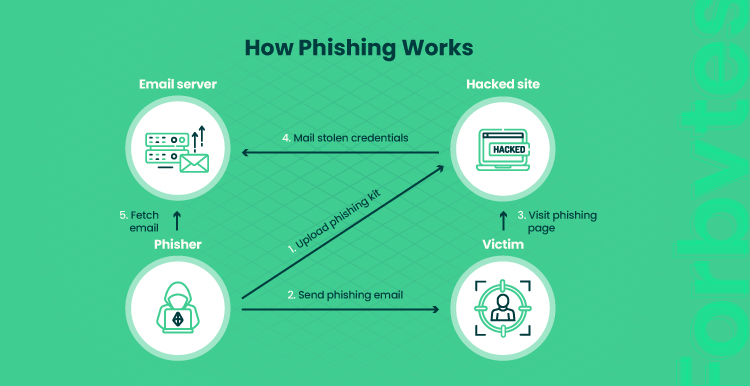
In 2020, phishing and pharming were the dominant types of e-commerce security attacks, affecting more than 240 000 victims. In a phishing scheme, a user gets a message that manipulates them to disclose their data. These can be social security numbers, credit card details, bank account info, and so on.
As a result of phishing attacks, a penetrator gets access to the financial resources of a user. They bypass ID verification and take over sensitive information.
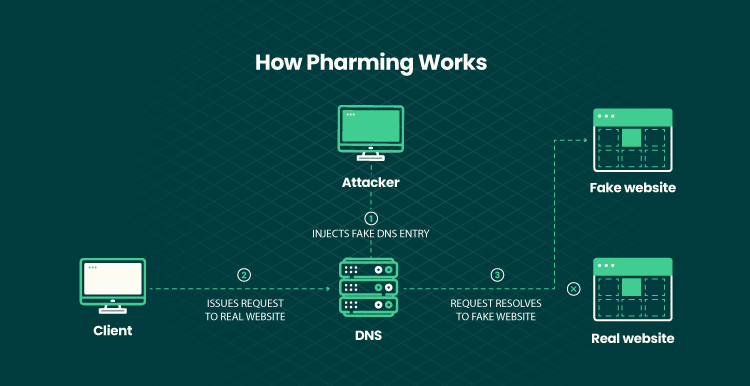
Meantime, pharming lies in redirecting users to fraud websites (that resemble the real ones) or proxy servers. In pharming, penetrators make use of Domain Name Service (DNS) to perform DNS spoofing and DNS cache poisoning.
DNS spoofing is based on the recursive query performed to an upstream DNS server. This, in turn, resolves the domain IP address and makes the name server open to DoS or cache poisoning attacks. In cache poisoning, a penetrator uses the cache to translate domain-IP mapping till they reach the Time-To-Live metric (TTL).
Phishing and pharming use a combination of tech and social skills. Such skills are applied to get unauthorized access to a third party’s sensitive data.
E-Skimming
In November 2021, e-skimming fraudulent activities increased by 48%. E-skimming is one of the relatively new and maliciously clever e-commerce security issues. It can be performed in different ways. One of the sophisticated approaches is infecting checkout pages with special malware. Attackers steal the payment data of customers who are making orders.
So, not only are users completely unaware of their data being stolen but their financial security is being compromised as well. For example, during Thanksgiving, 780 consumers of a Smith & Wesson company became victims of such attacks.
Try to prevent e-commerce security concerns associated with e-skimming. Use only secure payment gateways in your online store.
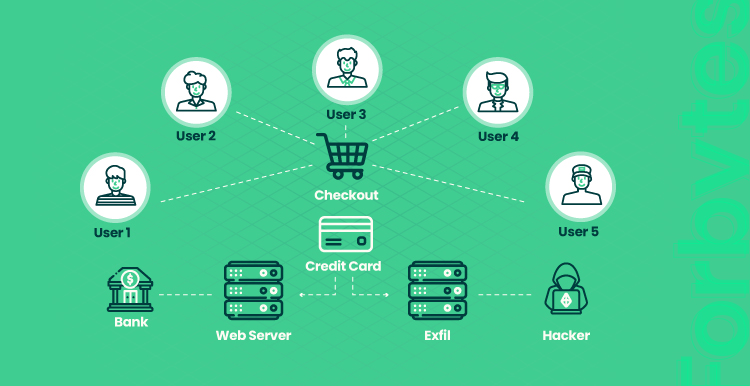
There’s a more brute-force approach to e-skimming. It involves redirecting users to third-party services that mimic the checkout page. Less tech-savvy or inattentive consumers won’t notice that something fishy is going on.
DoS and DDoS
Some things are just like classical music — always relevant. Time passes by, and DDoS attacks are still effective and often used as a means of making the lives of online retailers harder. One of the reasons for such lasting popularity of DDoS attacks is the straightforward simplicity of this exploit.
In 2021, the target sector of DDoS and DoS attacks was financing, which is tightly linked to e-commerce. DoS attack unfolds in the following way. A third party finds network vulnerability or writes a small loop intended to request a website’s home page. The more requests of this type come to the server, the more it slows down and becomes unable to process real customer requests. For businesses accepting many credit card transactions per hour, this may result in financial losses.
The more complex version of DoS is a DDoS attack, which stands for distributed denial of service. This is a coordinated security breach performed by multiple computers.
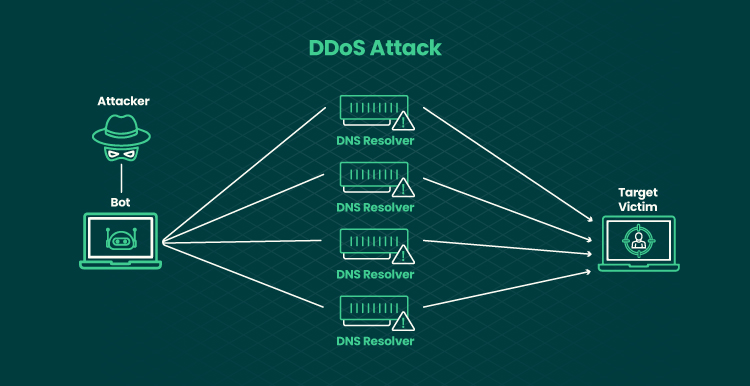
Usually, DooS attacks target one of the two aspects: OS bugs or network limitations. On the main computer, a penetrator installs a DooS software communicating the commands to other agent computers. These computers function as platforms for mini-attacks. The victim website overloads and crashes because of the hundreds or even thousands of multiple requests to the server. Because of the overload, legitimate users are unable to access the needed services.
Social Engineering Cyber Attacks
More than 90% of ecommerce security attacks now involve social engineering. Social engineering is an umbrella term. It refers to using social skills to manipulate users to perform certain actions. This may be disclosing cardholder data, opening access to the network, opening insecure links or messages, revealing passwords, etc.
An example of social engineering fraud that nearly everyone has dealt with is a fake call. For instance, from the so-called bank representatives who ask you to reveal your credit card data.
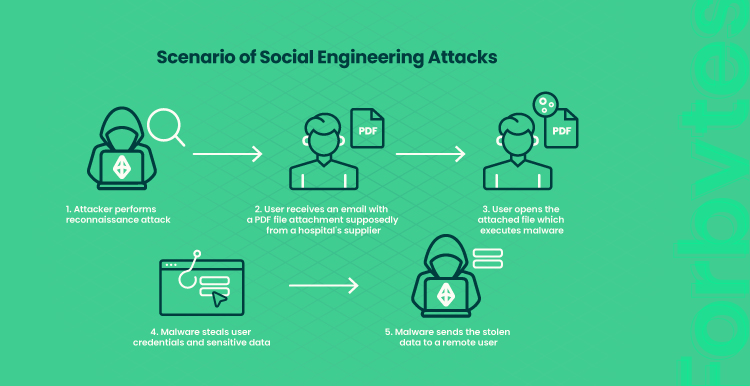
The main idea behind this notion is to use social skills to reach fraudulent goals. Social engineering frauds do not require profound tech skills. Neglection of cyber security in e-commerce or lack of awareness may result in e-commerce security breaches of this kind.
Cracking
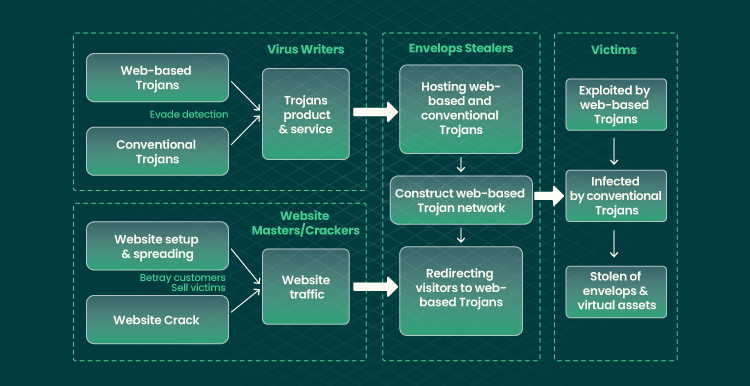
Let’s move to another common security issue in e-commerce. Cracking is the act of breaking the security of a website to perform malicious actions. Crackers intrude on a system in an unauthorized way. They modify or change configurations, features, or actions to bypass security checks. Their ability to break encryption or build tools that break protective algorithms may lead to a meltdown. As a result of such actions, frauds get the opportunity to misuse, manipulate, damage, or steal data.
The most common type of data that crackers are interested in is personal data. This causes ecommerce challenges not only for the company owning such data but also for customers and all people who interact with the company.
Here’s the representation of how crackers implement their malicious requests in practice.
Malware
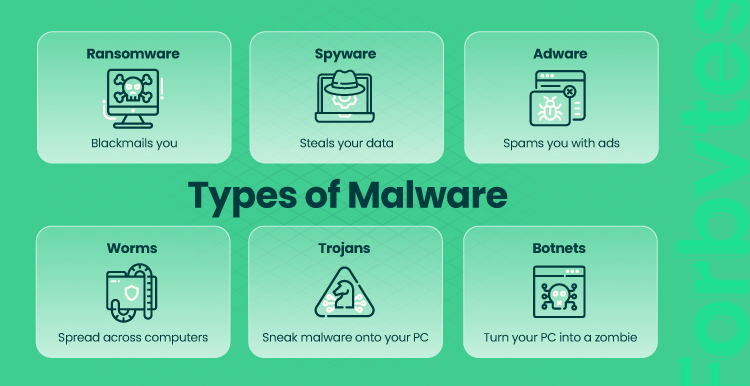
Malware comes in an incredible variety of “tastes and flavors.” Overall, any piece of software the purpose of which is to harm or compromise your system is malware. Malware can differ in complexity and efficacy. Malware attackers can disrupt the work of an online shop and steal or manipulate data. They hack passwords or gather information about your operations. What’s more, they can send e-commerce security messages to your customers on your behalf.
Here’s the classification of the most common malware cases:
When talking about ransomware, the frequency of this e-commerce security threat increased by 90% in 2021. Here’s how this most common type of malware works:
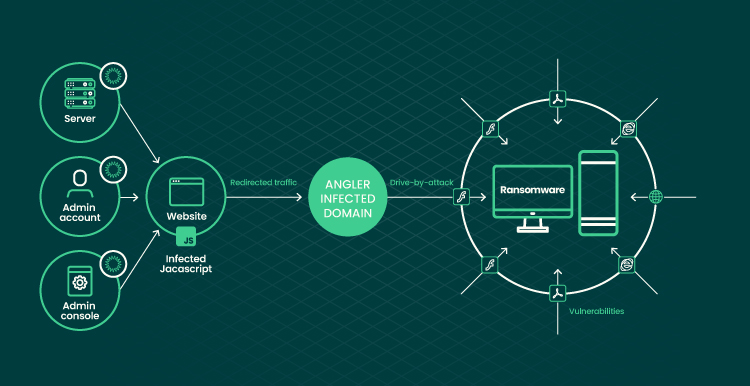
Overall, malware is not to be underestimated. Regular e-commerce cyber security updates will ensure good protection against malicious software.
Cyber Security for eCommerce: Tips for SME
There are three golden tips. Improve password security, use biometrics, and integrate multi-factor authentication software. Here is how some of the countries implemented these security measures to protect user accounts in 2021:
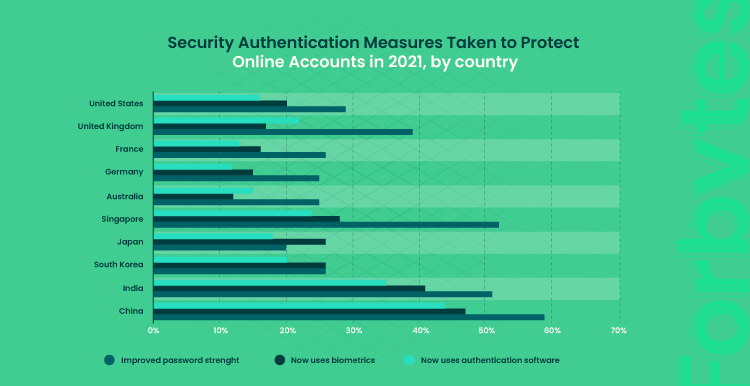
Also, make sure that your development team follows the standards of writing code. Profound testing of the software will also minimize security threats.
Above that, there are several eCommerce cybersecurity recommendations to keep in mind.
- Password complexity. Encourage your users to come up with complex passwords. Use long passwords (a bare minimum of 8 symbols). Ask customers to include lower- and upper-case letters, as well as numbers or other symbols. Such passwords will be very difficult to hack. The same applies to your employees, and especially administrators.
- Authentication. Implement multi-step authentication such as face ID or fingerprint scanner.
- SSL certificates. Never forget to update them timely.
- Educate your customers. Keep your clients aware of e-commerce security risks and identity theft cases. If your company doesn’t send certain types of emails, inform your customers about it. Encourage users not to follow third-party links from your e-commerce store. Conduct an audit of their online activities once in two weeks, for example, to detect suspicious actions.
- Manage data effectively. Delete all irrelevant data from your databases and don’t store data duplicates. You have to ensure flawless security of database scripts. Audit database log files regularly to detect unauthorized log-ins.
- Monitor the online shop’s performance. Review third-party integrations and react to malicious traffic. If any suspicious activity is present, inspect it.
- Keep your policies updated. In case of updating your eCommerce business, conduct a thorough QA check to determine any new weaknesses. After a change takes place, adjust your policies on hardware and software configuration and use.
- Prevent data loss. Make backups of valuable data using a secure storage space.
- Use a reliable eCommerce platform. Build your online store using only secure solutions. An example of a secure and reliable e-commerce platform is Magento. It offers numerous security extensions to help businesses feel safe about their data. And if you have an e-commerce site but the platform you use cannot grant you security, consider ecommerce replatforming.
- Ensure regulation compatibility. Make sure your eCommerce business complies with the e-commerce security regulations. For example, general data protection regulation (GDPR) — if you operate in the European market.
- Eliminate problems promptly. If DDoS attacks or sharp traffic fluctuations bother you, implement CDN. This refers to a content delivery network (which optimizes the load on your system between different servers).
Competency of Employees: Last Line of Defence
This point is often omitted. But at the end of the day, your online store is as secure as your least experienced employee is knowledgeable about common e-commerce security threats and best cybersecurity practices.
Proper training is a sure-fire solution to lots of security issues in e-commerce. Instruct every new employee who has access to information that can compromise your company’s security. They should know how to behave and manage their data.
The training should not only explain how to handle passwords and accesses but also give some communication tips. Some people specialize in the exploitation of digital systems by getting valuable information out of workers during casual conversations. Without the proper knowledge, it’s difficult to notice when you’re being used for information extraction and not a simple chit-chat.
Establishing a proper training period will cost you some time and money. But the benefits are incredibly far-reaching and invaluable to your retail business security. Also, proper HR and crisis management are important to any company. They help avoid employee frustration and prevent them from sharing sensitive data with third parties.
Wrapping Up
The security issue in e-commerce can be discussed from the viewpoint of a user and a service provider. On the one hand, users of e-commerce sites face security threats on a daily basis. On the other hand, businesses need to conduct a security audit and try to eliminate or at least decrease e-commerce risks.
The measures for maintaining privacy in e-commerce include the use of web seal assurances, two-factor authentication, cross-site scripting, security certificates, digital signatures, the integration of information security management systems, etc. As you see, e-commerce cybersecurity goes far beyond brute force attacks. It’s very important for companies that plan to scale and build trusted relationships with their audience.
If you need some tips on how to find a trusted ecommerce development partner to help you establish multi-layer security, check our 7-step guide.
Forbytes is a team of real e-commerce nerds who may help you make your online store better: from building a robust and secure e-commerce solution from scratch to choosing anti-malware software for your existing website. Get to know us — and let’s talk.

Our Engineers
Can Help
Are you ready to discover all benefits of running a business in the digital era?

Our Engineers
Can Help
Are you ready to discover all benefits of running a business in the digital era?








