When outsourcing started gaining popularity, DPA was among complementary, extra security measures. But now, it is an integral part of the interaction with third parties and a lawful data process.
How can you make sure that you choose a reliable outsourcing partner who’ll keep your data management safe? What is a DPA and why do you need it? This is what we will answer in this article.
Data Processing by a Third Party: Why You Should Care
If you know the connection between secure data processing and risk elimination, go to the next section. If you are still confused about the notion of a data protection agreement and data protection impact assessments, let’s dwell on the topic and make everything clear.
Once again, data protection is now one of the top priorities when it comes to cooperation with third parties. High-level organizations and governments put efforts to ensure maximum protection for enterprise and personal data. The European Union is no exception.
In 2016, the EU developed the General Data Protection Regulation or GDPR. GDPR is a set of rules concerning personal data transfer and processing. The primary goal of GDPR is to set a safe environment for international cooperation and business. Two years later, GDPR came into action with impressive results. In 2017, businesses employed nearly 83,000 Data Protection Officers. So far, this figure has risen by almost 700%.
Below, you can see what GDPR rights are exercised most frequently:
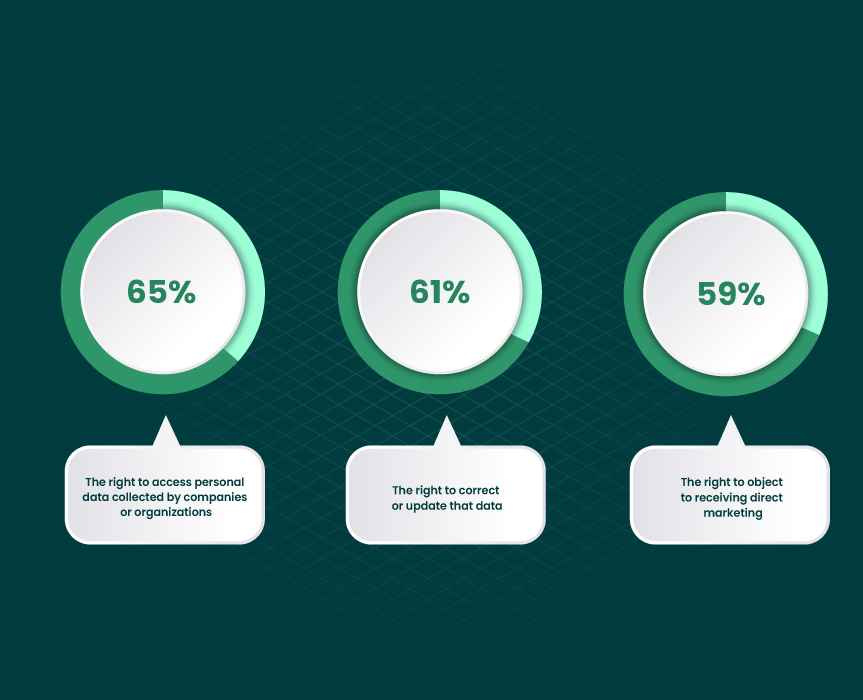
Generally, there are three important aspects of data protection:
- availability;
- integrity;
- confidentiality.
When one of the aspects goes out of control, the rest are inevitably affected. Insecure personal data processing may result in data breaches, financial losses, and harmed reputation. This is why you should pay close attention to the data protection guarantees you are given when hiring an outsourcing partner.
Now, we will answer the question “What is data processing?” for two types of stakeholders.
What does third-party data processing mean for a business owner?
As a business owner, you bear responsibility for choosing a reliable outsourcing partner that will keep your data safe. A third party should take data protection seriously. They have to clearly define the scope, reasons, and limits of their data processing activities. Your partner has to legally ensure non-disclosure of GDPR-related data. You may choose between the offshore, onshore, and nearshore partnership.
Offshore vendors are located abroad, outside of your country and bordering countries. The offshore partnership is an affordable way of finding a trusted outsourcing company. If you are looking for a partner in Ukraine, check out the list of the best offshore software development companies here.
Onshore companies are based in the same country as you. Forbytes, for instance, is an onshore partner for the US and Sweden businesses. By choosing an onshore partnership, you get more confidence in data protection. Of course, provided that you know how laws work in your country.
A nearshore partner is located in adjacent countries. The benefit of choosing a nearshore partner is the shared mentality. The latter, in turn, results in effective business communication and a clear understanding of the project goals. Wondering which nearshore partner to choose? This list may help.
When considering a particular country for outsourcing, pay attention to how personal data is secured on a legal level. Study the figures associated with a particular country. Analyze the frequency, cost, and outcomes of data breaches for the location of interest. It will help you find a reliable outsourcing company in this region and feel safe about your data security.
For example, you can analyze the overall value of GDPR fines imposed in 2018-2020 in certain countries:
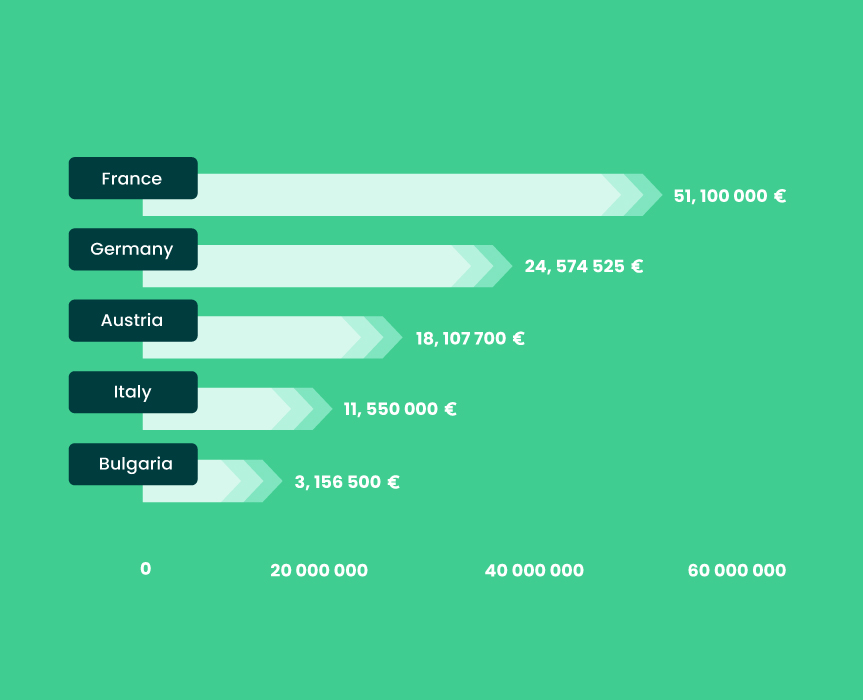
What does data processing mean for an outsourcing partner?
Suppose that Company A hires Company B to build a CRM system for an ecommerce project. Developing such a system presupposes that Company B gets access to clients’ data. In the eyes of a client, Company A is a guarantor of data safety. In the eyes of Company A, Company B has to guarantee this, too. Both act as data protectors. This rule is even stated in GDPR, which indicates that both parties are responsible for secure data processing.
So, what can an outsourcing partner do from their side? To ensure the security of their projects, they have to start with their back-office security. Outsourcing companies should ensure the highest level of cybersecurity for their data. Penetration testing and vulnerability tests are great ways of checking the company’s level of protection and identifying security gaps.
Also, they have to have a well-composed privacy policy, with a detailed description of all third-party services having access to their data. And, finally, they have to be ready to sign a Data Processing Agreement (DPA) with their clients. You’ll read about the data processor meaning later. Now, let’s figure out why clients need DPA at all.
DPA is a Way to Keep Your Data Safe
What is DPA? DPA definition stands for Data Processing Agreement. DPA defines if all data-related activities are compliant with GDPR policy. By signing a DPA, both parties protect project data and get the guidelines for data breach prevention and elimination.
When is a data processing agreement required? When you want to get high-level assurance of data security. A data privacy agreement is not attached to a specific form. It can be either written or electronic, either a part of the general contract or a separate document. Everything depends on the practices the parties apply. The form of DPA (Data Processing Agreement) does not affect its power. But its contents do.
What DPA Should Look Like
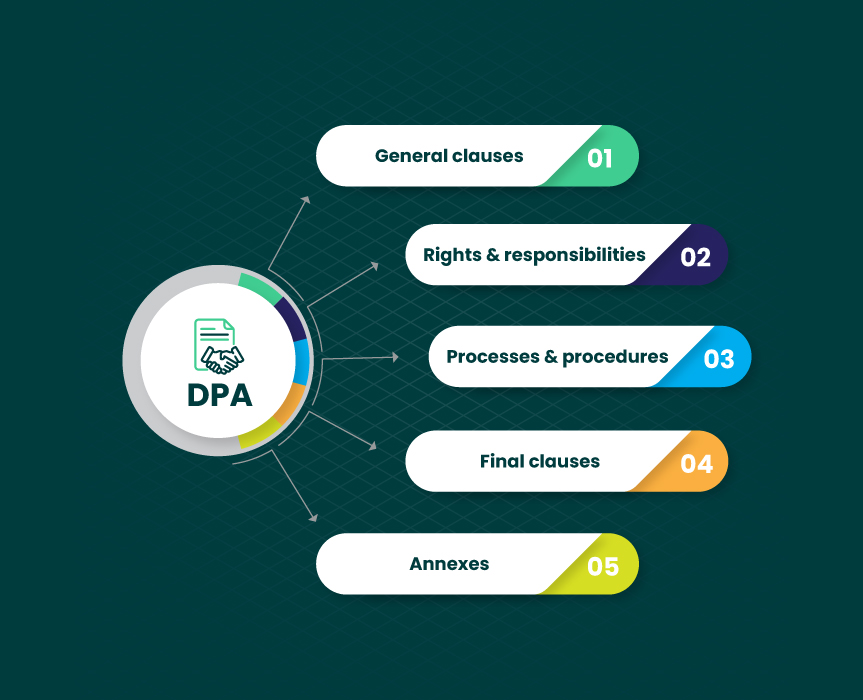
Now, you know the answer to the question “What does DPA stand for?” Let’s then look at the basic elements usually mentioned in DPA. They may be complemented by additional ones, depending on the parties’ concerns, requirements, and goals. Before signing a Data Processing Agreement with an outsourcing company, make sure that the agreement includes the following:
1. General clauses
Your DPA should name who is:
- Data controller. Data controllers are stakeholders who entrust their data to a third party.
- Data processor. What is a data processor then? Data processors may be people or a company that processes data on behalf of the data controller.
Also, the first part describes the following:
- Types of DPA data (data that will be accessed by a third party).
- Subjects of data.
The latter may include various categories of people or companies whose data will be processed. For example, these may be your clients or partners.
General clauses should also include the description of:
- Goals of data processing.
- Scope of customer data.
- DPA software (data processing systems, tools, or software solutions).
- Duration of processing personal data (or enterprise data usage).
- Data storage description.
And what about DPA (data privacy agreement) duration? Outline the following:
- Duration of the agreement.
- Conditions of agreement termination.
Do not forget to mention that personal data processor is obliged to remove your data from their storage once the DPA is terminated. That is, data transferred to their systems have to be permanently deleted in this case.
2. Rights and responsibilities of stakeholders
This part consists of:
- The rights and responsibilities of a data controller.
Here, your rights and responsibilities as a data controller will be described. Why are we talking about duties? Because DPA states that you have to observe the rights of data subjects and make sure that a processor handles data in compliance with terms, processing instructions, and regulations. So, you have the responsibilities as well.
- The rights and responsibilities of a data processor.
This part of the document describes the rights and responsibilities of data processors. What does a data processor do? Their main duty is to ensure ongoing data security and eliminate the risks of a data breach. In case the breach occurs, a data processor has to provide you with an effective response. Data processing companies are also obliged to comply with data subjects’ rights.
A data processor has to keep a record of their data-related activity and allow you to conduct an audit of DPA compliance. They are not allowed to involve any third-party service provider in data processing without your consent.
3. Procedure and process description
The third part is devoted to measures taken by all parties to ensure data protection and secure data processing in outsourcing. It is preferable to mention both of the following:
- Organizational aspect of data protection and agreement compliance.
- The technical side of the same aspect.
4. Final clauses
Here, companies usually mention:
- Conditions under which the agreement can/cannot be changed.
- Data Processing Agreement superiority over other documents.
5. Annexes
Annexes include any supplementary documentation essential for the execution of Data Processing Agreements. For example:
- Tables with step-by-step process descriptions.
- Audit results.
- Lists of GDPR sections that are of particular importance.
That’s it. Of course, there are a lot of DPA contract templates available online. When choosing a data processor agreement template, make sure that all essential elements are included. It will help you prevent confusion and eliminate risks.
Remember: spending some time on the customization of a template is safer than neglecting important aspects of the agreement.
Checklist for Choosing a Secure Data Processor
You already know what a good Data Processing Agreement looks like. But before signing the agreement, make sure that your software development partner is reliable. Our quick checklist may help you identify the weak sides of your data processor and mention these points in the DPA agreement.
Here are the questions to ask:

1. Does a company have a registered office in the European Union?
Choose an outsourcing partner that has a presence in the European Union. It will give you more certainty about the security of the services your partner provides. Also, it will help you make sure that GDPR compliance and data privacy exist not only on paper but also in practice.
2. Is a company GDPR-compliant?
Check the privacy and data protection policy of the vendor. Check the list of the third parties that have access to the company’s data. In case you have some security doubts, discuss the issues in advance. Sometimes, it is even better to outline controversial points in the agreement or contract.
3. What strategy for information security does it have?
Ask your potential partner about the ways of ensuring information security. Do they have a security strategy? Ask them who is responsible for securing data in their company. You should see the readiness of your partner to answer security-related questions.
4. What are the methods of storing data?
It is nearly impossible to ensure the safety of consumer data if a company fails to ensure the safety of its data. Ask your partner where their data is stored. Do they use an on-premise type of storage or a cloud-based solution? If they use the latter, how reliable their cloud provider is?
5. Is data protected on the technical level?
Ask the outsourcing company about the technical side of data protection. What type of hardware do they use? How do they ensure secure authorization? A reliable partner keeps a record of authorized devices and controls the inventory.
6. How does a company prevent software vulnerabilities?
When developing a software product, a professional software development team sticks to the full-cycle method. That is, apart from building the very product, a company also provides support and maintenance. So how does your partner ensure the security of the products they make? Do they have some response strategy in case of reporting data breaches?
7. What strategy for infrastructure protection does it pursue?
The final question will help you understand how the company deals with data breach prevention. How does your potential partner back up their data? How do they protect their devices from malicious attacks?
Final Thought
This article comprises everything you should know about the DPA meaning. In business, data safety is of the utmost importance both for you and your clients. You should be aware of the adverse outcomes of personal data breaches and put maximum effort into preventing such situations from happening. A great way to reduce risks is to hire a trustworthy software engineering vendor.
We hope that the given info will help you choose a reliable software development company providing high-quality services. Contact us if you need more detailed and guided answers.

Our Engineers
Can Help
Are you ready to discover all benefits of running a business in the digital era?

Our Engineers
Can Help
Are you ready to discover all benefits of running a business in the digital era?








