In 2023, the U.S. experienced 242 supply chain attacks, a 115% increase from the previous year. With cyber threats becoming more common, it’s no surprise that 44% of organizations are ramping up their cybersecurity budgets.
Experts are concerned too: 84% of IT professionals believe that software supply chain attacks will be one of the biggest threats in the coming years. This should be a wake-up call for all of us. What do you think – are you prepared to tackle these growing risks?
Hackers are always hunting for weak spots, and even one breach can cause massive disruptions, financial losses, and harm to your reputation.
Serene Davis, Global Head of Cyber, said it best: “A breach alone is not a disaster, but mishandling it is.” This shows how important it is to not just prevent attacks but also have a solid plan to respond quickly. The way you handle a breach can make it either a small roadblock or a major crisis for your business.
The good news? Protecting your logistics doesn’t have to be complicated. In this article, we’ll explain why supply chain cyber security is more important than ever and give you simple, actionable tips to stay safe. Let’s get started!
What Is Supply Chain Cyber Security?
If you’ve ever dealt with supply chain management, you’re familiar with how it’s vital to protect it from attacks and other possible threats.
Supply chain cyber security is about protecting your supply chain from risks, whether it’s working with suppliers, vendors, or logistics partners. The idea is simple: identify, analyze, and reduce risks that come while cooperating with other companies. Supply chain cyber security involves ensuring strong safety for your software and services.
Since every supply chain is different and involves many players, there’s no one-size-fits-all solution. Building a solid security strategy means using good risk management practices, having layered cybersecurity defenses, and following rules set by security agencies. It’s all about staying prepared and protected.
Contact our team to learn more about supply chain cyber security and discover how we can help enhance your business’s safety.
Why Supply Chain Cyber Security Is Important for Your Business
Supply chain cyber attacks are a growing problem. Big attacks like SolarWinds and Kaseya show how hackers can cause huge damage by targeting one company and spreading the impact to others.
For example, the SolarWinds attack compromised its Orion software updates, affecting over 30,000 organizations, including U.S. government agencies. In the Kaseya attack, hackers exploited vulnerabilities in their VSA software, impacting about 1,500 businesses worldwide.
Here’s how attackers work: First, they infect software updates with harmful code, like in the SolarWinds attack, which was then sent to thousands of customers. Second, they target open-source libraries, spreading viruses. Since most apps rely on many libraries, the threat can spread quickly.
Supply chain cyber security helps businesses stay safe by monitoring software dependencies and fixing issues before they turn into major problems. It’s about staying one step ahead of attackers and protecting your systems.
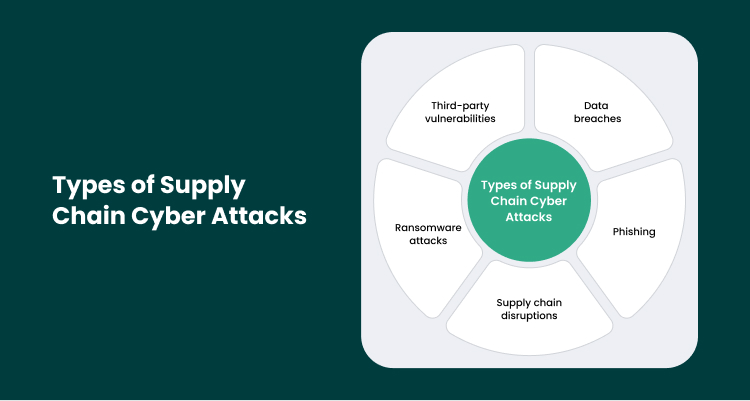
Main Types of Supply Chain Cyber Attacks
Supply chain cyber attacks happen when hackers take advantage of the trust organizations place in their partners and software. Here are some key threats you need to be aware of:
- Third-party vulnerabilities: Many supply chains depend on external vendors, which can sometimes have weaker security. Hackers can use these weaker links to access sensitive data or spread malware.
- Data breaches: A data breach can cost millions and expose sensitive customer data. Cybercriminals target weak spots in a supply chain’s digital systems to steal data.
- Phishing: Phishing attacks are when hackers trick employees into revealing sensitive information, like login details, through fake emails or messages.
- Supply chain disruptions: Cyberattacks can also target infrastructure like transportation or manufacturing systems, causing big delays and shortages.
- Ransomware attacks: Hackers lock data and demand a ransom to unlock it. Supply chains are prime targets because they rely on timely data.
So see how many cyber crimes can threaten your supply chain and disrupt its work. That’s why you should understand these risks, be prepared to address them on time, and ensure supply chain cyber security.
Protect your business with Forbytes. We implement advanced security measures to prevent supply chain attacks and safeguard your data. Reach out to learn more.
Real-World Examples of Cyber Attacks on Supply Chain
It may seem that cyber attacks on the supply chain do not occur until they touch you. So, you should be aware of these cases to understand the risks for your business and learn how to achieve supply chain cyber security:
ASUS (2019)
Backstory:
In 2019, hackers attacked ASUS by creating a fake version of their Live Update software, which appeared real but had malware inside. It was sent to users through ASUS’s update system, targeting only a small group. The malware went unnoticed for a while because it looked like real software.
Lessons Learned:
What can we learn from ASUS’ experience? Protect your digital signing processes and regularly check certificates to prevent misuse. Always verify third-party software and updates for vulnerabilities before using them. Set up monitoring systems to catch unusual activities early and stay ahead of potential threats.
GitHub (2020)
Backstory:
In 2020, malware called Octopus Scanner targeted open-source software on GitHub. It infected specific projects, adding harmful code. When developers downloaded these projects and built software, the malware activated. This let the malware spread during the build process and gave hackers access to sensitive information on infected systems.
Lessons Learned:
What can you take from GitHub’s experience? Use tools to detect malicious code and unusual behavior in repositories, helping to prevent infections. Regularly update and audit third-party libraries and components to identify and address risks.
SolarWind (2020)
Backstory:
In December 2020, hackers targeted SolarWinds by adding malicious code to its Orion software updates. This malware, called SUNBURST, was sent out as part of regular updates, affecting about 18,000 customers. The attack went unnoticed for months and was finally discovered by cybersecurity firm FireEye when it detected unusual activity in its network.
Lessons Learned:
This case shows why supply chain cybersecurity is so important. Make sure vendors and partners follow strict security rules. Also, use advanced tools to spot hidden and complex attacks.
Codecov (2021)
Backstory:
In early 2021, hackers exploited a weakness in how Codecov built its Docker images to attack the code coverage tool. They injected malicious code into Codecov’s Bash Uploader script, which customers then used in their CI environments. The malware stole sensitive data, such as tokens and keys, and sent it to the attackers’ server. The breach went undetected for months until a customer spotted a discrepancy in the script’s hash.
Lessons Learned:
From Codecov’s example, keep these points in mind. First, always check your code with checksums to ensure it’s not tampered with. Second, secure your build environment and regularly check for vulnerabilities. Lastly, monitor your CI/CD pipelines for any unusual changes or activity.
These examples underscore the importance of robust supply chain security measures to protect against evolving threats.
Best Practices for Enhancing Cybersecurity of Supply Chain
From the real-world examples mentioned above, it’s obvious that supply chain attacks can seriously impact businesses. But there are steps you can take to prevent them or reduce the damage if they happen. Here are some simple and effective practices to ensure your supply chain cyber security:
- Limit access: Give people, apps, and systems only the access they need to do their job. This helps reduce the risk of damage if something is compromised. Limiting access makes it harder for unauthorized users to get into sensitive data and systems, so it’s easier to control and fix security problems quickly.
- Break up your network: Divide your network into smaller, secure areas based on their purpose and trust level. For example, keep sensitive data and important systems separate from less secure parts. This makes it harder for hackers to move around if they get into one area.
- Build security in: Add security checks early in development to catch and fix vulnerabilities quickly. This proactive approach strengthens your software’s security and reduces the cost of fixing issues later. Regular testing during development ensures a safer final product and better protection for your systems and data.
- Scan for weak spots: Conduct routine scans of your applications to identify vulnerabilities. This helps you find and fix problems quickly, even in third-party code. Scanning often makes your system safer and protects user data from breaches.
- Automate defense: Set up tools and systems that automatically detect and stop threats before they cause damage. Automation helps you respond quickly to risks, reduces the chance of human error, and keeps your defenses active 24/7. Combine proactive strategies like firewalls, intrusion detection systems, and real-time monitoring to strengthen your security.
- Hunt for threats: Actively look for hidden threats in your systems. This can help you catch attackers early, especially those exploiting supply chain vulnerabilities. Use tools like threat intelligence platforms, behavior analysis, and anomaly detection to uncover suspicious activities.
By adopting these practices, you can strengthen your defenses and stay ahead of potential threats.
Achieve Robust Supply Chain Cyber Security with Forbytes
Supply chain cyber attacks are a big threat to security, with risks like data theft and ransomware. To protect against them, start securing your software from the beginning. Scanning code for weaknesses during development and keeping track of them after deployment helps spot problems before they cause damage.
At Forbytes, we offer technology due diligence services to perfect your tech solutions and operations and improve your digital brand and the quality of tech services you provide. So, with our expertise, you can achieve robust supply chain cyber security and prevent emerging threats.
Contact our team to understand how we can improve your app security and make it less vulnerable to cyber attacks.